ClickFix, a social engineering tactic that has been targeting both Windows and Mac users since early 2024, continues to evolve.
Just last month, I reported on how attackers were using fake CAPTCHA prompts to trick Windows users into installing malware themselves.
Now, that same trick is being turned against macOS. Cybersecurity researchers have uncovered a new campaign using ClickFix to deliver Atomic macOS Stealer (AMOS), a powerful information-stealing malware targeting Apple systems.
SPOT FAKE ONLINE STORES, AVOID FACEBOOK SUBSCRIPTION SCAMS

What is ClickFix malware, and how does it work?
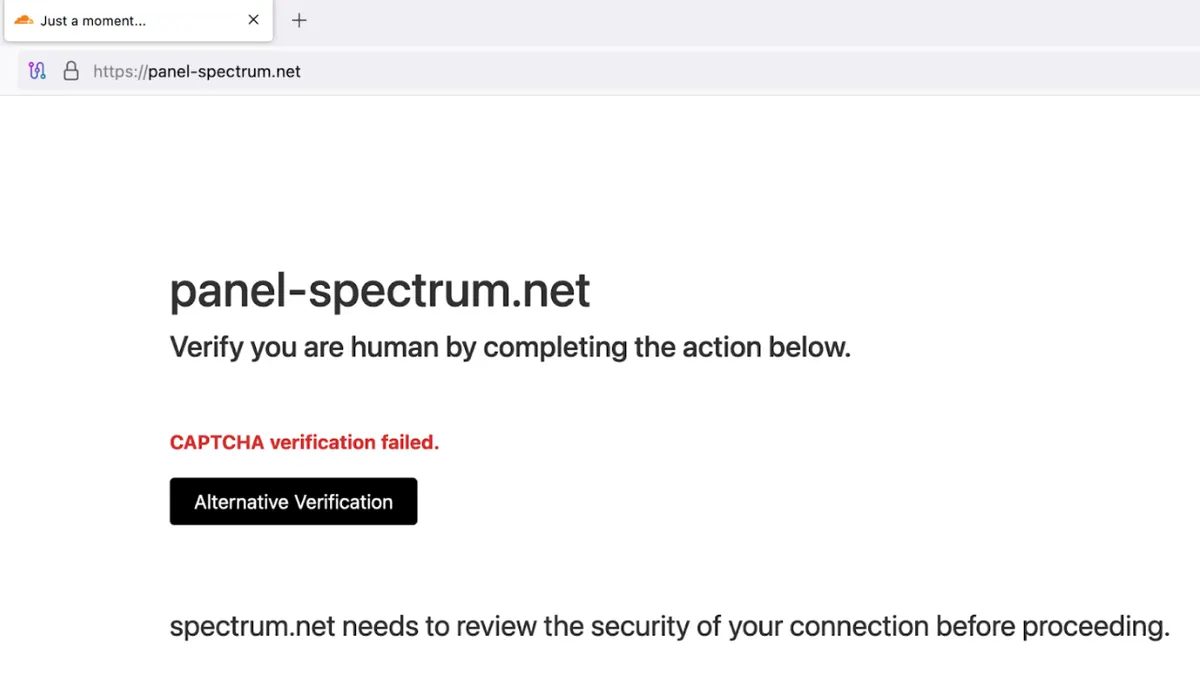
Security researchers at CloudSEK have identified a new threat targeting macOS users through imitation and deception. The campaign uses a technique known as ClickFix to lure victims through fake online verification prompts. This time, attackers are spoofing Spectrum, a major telecom provider in the United States. They use fraudulent domains that closely resemble Spectrum’s real support portals. These include misleading addresses like panel spectrum net and spectrum ticket net.
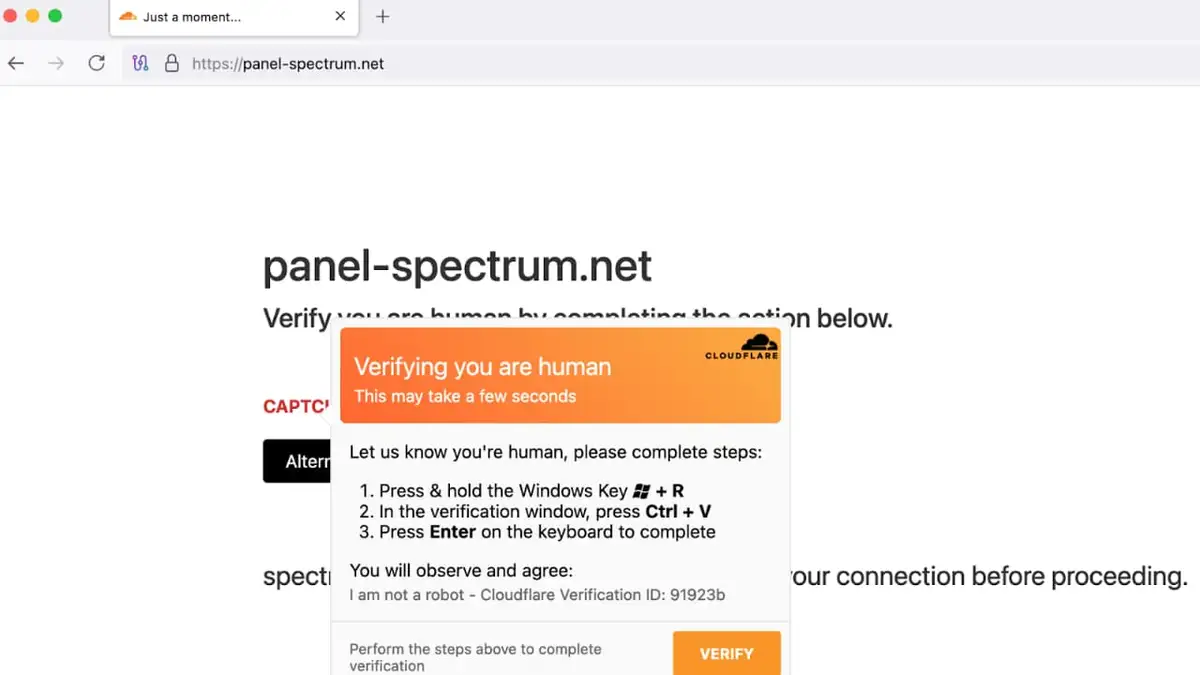
Visitors to these sites are shown a standard-looking CAPTCHA box, asking them to verify their identity. When they do, the site displays a fake error message that says the CAPTCHA failed. Users are encouraged to click a button labeled "Alternative Verification." This triggers a command to be copied silently to their clipboard. What happens next depends on the user’s operating system. On macOS, instructions guide the user to paste and run the command in Terminal. That command is actually a shell script designed to steal information and download malware.
The script is particularly dangerous because it uses legitimate macOS system commands. It asks for the system password, harvests credentials and disables security protections. It then downloads AMOS. This is a known information stealer with a history of targeting Apple devices. The malware collects sensitive data like passwords, cryptocurrency wallet keys, browser autofill data and saved cookies.
Researchers believe the campaign was created by Russian-speaking attackers. Clues include comments written in Russian found within the malware’s code. Analysts also noted that the delivery infrastructure was poorly assembled. Mismatched instructions appeared across devices. For example, Linux users were shown Windows commands. Mac users were told to press keys that only exist on Windows machines.
Sign up for my FREE CyberGuy Report
Get my best tech tips, urgent security alerts, and exclusive deals delivered straight to your inbox. Plus, you’ll get instant access to my Ultimate Scam Survival Guide — free when you join.
OUTSMART HACKERS WHO ARE OUT TO STEAL YOUR IDENTITY
Why ClickFix attacks are so effective
ClickFix is a social engineering method that has rapidly gained popularity among cybercriminals. It relies on users trusting what they see and blindly following simple instructions. In this campaign, the attacker’s goal is to make the victim execute the infection process themselves. Once the user follows through, the system is compromised without needing a traditional exploit.
Researchers believe ClickFix has been active since at least March 2024. I first reported on it in June 2024, when attackers used fake error messages from Google Chrome, Microsoft Word and OneDrive to push their payloads. Victims were shown prompts offering a "fix," which copied a malicious PowerShell command to their clipboard. They were then instructed to paste and run it in PowerShell or through the Run dialog.
By November 2024, the method had evolved further. A new wave of attacks targeted Google Meet users, beginning with phishing emails that mimicked internal meeting invites. These emails contained links that redirected to fake Meet landing pages designed to look like they came from the victim’s own organization.
MALWARE EXPOSES 3.9 BILLION PASSWORDS IN HUGE CYBERSECURITY THREAT
6 ways to protect yourself from ClickFix and similar malware
To protect yourself from the evolving threat of ClickFix malware, which continues to target users through sophisticated social engineering tactics, consider implementing these six essential security measures:
1. Be skeptical of CAPTCHA prompts: Legitimate CAPTCHA tests never require you to paste anything into Terminal. If a website instructs you to do this, it’s likely a scam. Close the page immediately and avoid interacting with it.
2. Don’t click links from unverified emails and use strong antivirus software: Many ClickFix attacks also start with phishing emails that impersonate trusted services like Booking.com or Google Meet. Always verify the sender before clicking on links. If an email seems urgent or unexpected, go directly to the company’s official website instead of clicking any links inside the email.
The best way to safeguard yourself from malicious links that install malware, potentially accessing your private information, is to have strong antivirus software installed on all your devices. This protection can also alert you to phishing emails and ransomware scams, keeping your personal information and digital assets safe. Get my picks for the best 2025 antivirus protection winners for your Windows, Mac, Android and iOS devices.
3. Enable two-factor authentication: Enable two-factor authentication whenever possible. This adds an extra layer of security by requiring a second form of verification, such as a code sent to your phone, in addition to your password.
GET FOX BUSINESS ON THE GO BY CLICKING HERE
4. Keep devices updated: Regularly updating your operating system, browser, and security software ensures you have the latest patches against known vulnerabilities. Cybercriminals exploit outdated systems, so enabling automatic updates is a simple but effective way to stay protected.
5. Monitor your accounts for suspicious activity and change your passwords: If you’ve interacted with a suspicious website, phishing email, or fake login page, check your online accounts for any unusual activity. Look for unexpected login attempts, unauthorized password resets, or financial transactions that you don’t recognize. If anything seems off, change your passwords immediately and report the activity to the relevant service provider. Also, consider using a password manager to generate and store complex passwords. Get more details about my best expert-reviewed Password Managers of 2025 here.
6. Invest in personal data removal service: Consider using a service that monitors your personal information and alerts you to potential breaches or unauthorized use of your data. These services can provide early warning signs of identity theft or other malicious activities resulting from ClickFix or similar attacks. While no service promises to remove all your data from the internet, having a removal service is great if you want to constantly monitor and automate the process of removing your information from hundreds of sites continuously over a longer period of time. Check out my top picks for data removal services here.
Get a free scan to find out if your personal information is already out on the web
MASSIVE SECURITY FLAW PUTS MOST POPULAR BROWSERS AT RISK ON MAC
Kurt’s key takeaway
Even experienced users can be tricked when malicious behavior is disguised as routine. The attack didn't just exploit a vulnerability in macOS, but also your familiarity with verification flows. As long as security instructions look like part of the usual experience, people will continue to run malicious code themselves. Mac users, like everyone else, need to treat every familiar-looking interface with a little more skepticism. Especially when it asks for your password.
Do you think tech companies are doing enough to stop malware like ClickFix? Let us know by writing to us at Cyberguy.com/Contact.
For more of my tech tips and security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter
Ask Kurt a question or let us know what stories you'd like us to cover.
Follow Kurt on his social channels
- YouTube
Answers to the most asked CyberGuy questions:
- What is the best way to protect your Mac, Windows, iPhone and Android devices from getting hacked?
- What is the best way to stay private, secure and anonymous while browsing the web?
- How can I get rid of robocalls with apps and data removal services?
- How do I remove my private data from the internet?
New from Kurt:
- Try CyberGuy's new games (crosswords, word searches, trivia and more!)
- CyberGuy’s Exclusive Coupons and Deals
Copyright 2025 CyberGuy.com. All rights reserved.







